
Looking for ways to help your team accomplish more? Consider equipping their workspaces with additional monitors. S...

What Is the Big Picture in Terms of Cybercrime in 2018? The past few years have revealed trends that show us cyberc...

The network is a vital part of the IT environment – at its core, what are the most important elements of network ma...

Users of Facebook Messenger, which number over 1.2 billion people worldwide, now have a new feature that makes life...

There is a lot to love about the work that you do, and hopefully, your technology is part of that. Loving your IT m...

Apple is yet to disclose how much it is going to reward a 14-year-old U.S. teenager for discovering a massive secur...

Microsoft’s Visio Visual and Power BI are two extremely useful software tools that help business owners store, orga...

Cybersecurity threats have shown no signs of slowing down, and small and mid-sized organizations are expected to be...

Advanced Data Governance (or ADG) is a tool from Microsoft. Available to be used within Office 365, this tool assis...

You can create a data entry form in Microsoft Excel without using VBA or even recording a macro. If those terms don...
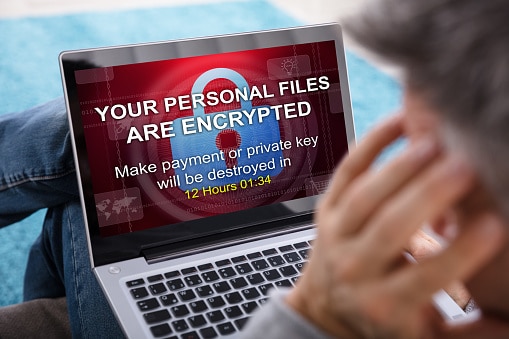
Ransomware. Ransomware. You have heard the word and know it involves a cyberattack. You assume from news reports th...

For over 30 years Cyclone Drilling, Inc. has taken pride in providing their clients with rigs that put safety and p...












