
Capital One Data Breach Affects More Than 100 Million Customers and Small Businesses in The U.S. & 6 Million in...

The cloud may still feel like a new technology – but in reality, it’s been around for more than 10 years now. Does ...

Phishing Attacks Target OAuth Credentials to Gain System Access Discover how an increasingly popular authentication...

5 Incredible Benefits of Effective Managed IT Services Managed IT services are one of the many ways an organization...

What Is Network Segmentation? Businesses that offer WiFi to their customers or have sensitive data needs should con...

Organization Shouldn’t Be Complicated Out of all of Microsoft’s Office programs, Excel is one of the most universal...

As the business world continues to evolve, digital transformation becomes even more important for every company, re...
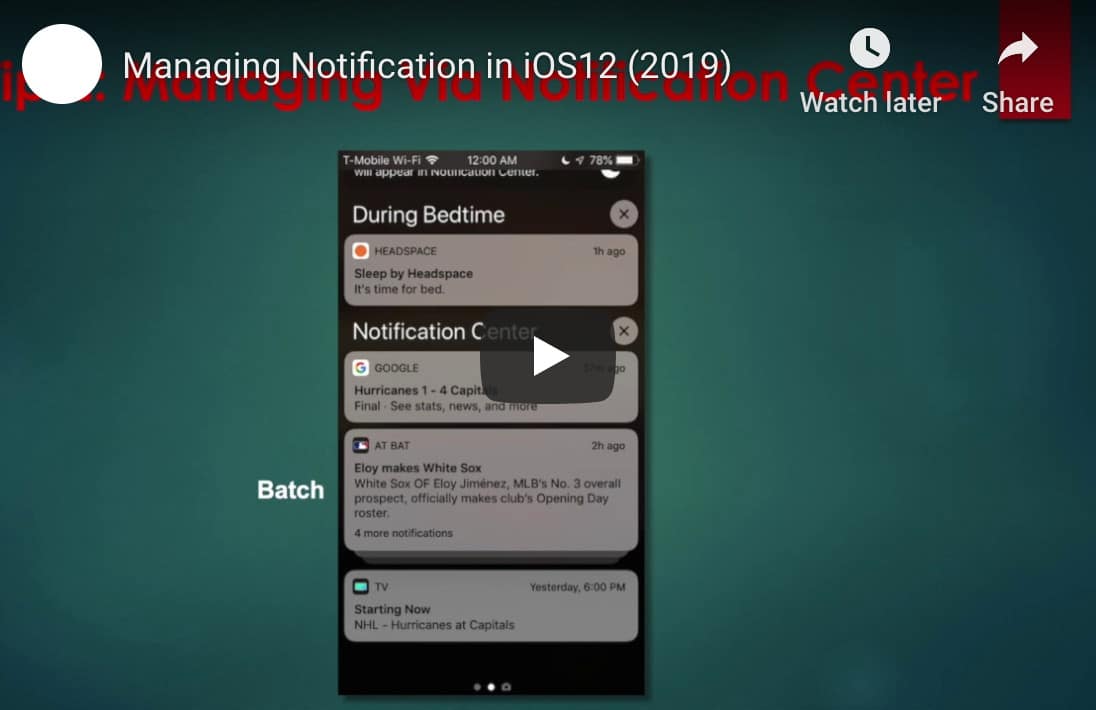
Apple’s mobile iOS operation system is one of the most popular platforms in the world. With more than 1.3 billion d...

How Do I Choose a Cloud Computing Model? No matter what your company or organization specializes in, it’s sure that...

We’re only halfway into 2019, yet data protection specialists and IT analysts have already seen an unfortunate spik...

What Are the Top Tips for Choosing the Best IT Company? Website outages, cybersecurity attacks, and any number of o...

Your MacOS Is Under Attack: 2019’s Biggest Malware Threats The Mac operating system (MacOs) has frequently been hai...












